Table of Contents
- What Is SASE and Why Does It Matter?
- Key Components of SASE
- Driving Forces Behind SASE Adoption
- Business Benefits of SASE Architecture
- Strategies for Implementing SASE Successfully
- Common Challenges and How to Address Them
- The Future of SASE and Digital Security
- Conclusion
What Is SASE and Why Does It Matter?
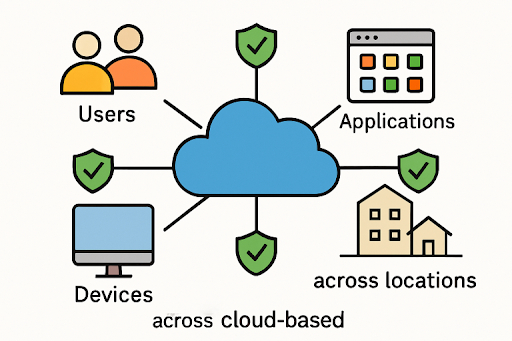
In today’s cloud-centric and remote workforce environment, ensuring consistent security and network performance is more challenging and more crucial than ever. Secure Access Service Edge, or SASE, is a comprehensive framework that unifies networking and security technologies into a single, cloud-delivered architecture. By converging these critical functions, SASE empowers organizations to securely connect users, devices, and applications—no matter their location—without sacrificing agility or performance. This architectural shift is foundational for modern digital business. The growth of distributed teams, increasing reliance on cloud-based services, and the escalating sophistication of cyber threats demand an evolution away from legacy security models toward more integrated approaches. SASE offers a standardized path to secure and optimize every edge of the network while delivering the flexibility and scalability modern enterprises need to keep pace with change.
Key Components of SASE
SASE solutions unite multiple technologies into a single, manageable platform. The primary components are:
- SD-WAN (Software-Defined Wide Area Network): Enhances connectivity by intelligently routing network traffic across multiple transports, improving performance and reducing dependency on traditional MPLS lines.
- Cloud-Delivered Security: Key elements include Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB), offering scalable, real-time protection regardless of user or application location.
- Zero Trust Network Access (ZTNA):Implements a strict identity verification process before granting access, shrinking the network attack surface by adopting a “never trust, always verify” stance.
Unified under a cloud-first model, these components streamline networking and security operations, reducing complexity and centralizing control for IT teams.
Driving Forces Behind SASE Adoption
Several compelling drivers are accelerating widespread SASE deployment. The shift toward remote and hybrid workforces has challenged traditional perimeter-based security, and the explosion of cloud services has rendered legacy hardware-centric solutions increasingly obsolete. Simultaneously, cybersecurity risks have grown more dynamic, with bad actors exploiting gaps between dispersed users, cloud apps, and insecure networks. Analyst firms emphasize that legacy architectures are ill-equipped to meet contemporary security and access challenges. Many organizations are rethinking their legacy infrastructures to achieve the agility, control, and end-to-end protection provided by SASE frameworks.
Business Benefits of SASE Architecture
The move to a unified SASE approach brings measurable improvements for enterprises seeking to accelerate digital transformation:
- Simplified Network Operations:Organizations reduce vendor sprawl and administrative overhead by consolidating security and networking functions into a single, cloud-driven solution.
- Agility and Scalability: SASE solutions easily scale to support global workforces, new branch locations, or changes in user demand without the need for complex hardware upgrades.
- Cost Efficiency: Shifting security and networking to a subscription-based model streamlines operations and enables predictable budgeting, reducing the need for expensive, on-premises infrastructure.
- Stronger Security Posture: Integrated security reduces attack surfaces and ensures threat protection is applied consistently—regardless of user location.
- Improved User Experience: Direct internet and cloud access reduce latency and provide a faster, more seamless experience for end users across devices and sites.
Strategies for Implementing SASE Successfully
Conduct a Comprehensive Assessment
Start by evaluating existing network and security architectures to identify gaps, bottlenecks, and inefficiencies. Map out user requirements, cloud use cases, and any legacy dependencies.
Define Clear Objectives
Establish business and security goals to guide the SASE transformation. Clear KPIs—such as risk reduction, performance improvements, or cost savings—help align stakeholders.
Select the Right Partners
Choose trusted vendors with proven SASE expertise. A vendor-neutral, platform-agnostic approach helps avoid vendor lock-in and supports future business needs as the threat landscape evolves.
Pilot and Train
Run pilot implementations in departments or branch locations to uncover any issues before full rollout. Equip IT and security staff with comprehensive SASE training to boost adoption and mitigate risks.
Phase the Rollout
Move beyond a “big bang” approach. A phased rollout, prioritized by risk or operational impact, minimizes disruptions and paves the way for continuous improvement.
Common Challenges and How to Address Them
Implementing SASE is not without potential stumbling blocks. Integration with existing assets, confusion over new policies, and change resistance are common hurdles. Open communication, transparent change management, and ongoing education are critical to address these. Leveraging automation can also simplify policy enforcement and streamline the transition. Successful SASE adoption often hinges on close collaboration between security and networking teams, ensuring that both groups are aligned on requirements and processes. Policy management can prove especially daunting as organizations adapt to a convergence of networking and security. Modern orchestration tools and automation can help reduce complexity, while clear communications about the rationale and benefit of SASE can alleviate resistance from internal stakeholders.
The Future of SASE and Digital Security
The SASE landscape is rapidly evolving as new threats and technologies shape enterprise needs. As hybrid and remote work remain entrenched, future SASE architectures will likely leverage advancements in artificial intelligence and machine learning for smarter, automated threat detection and response. Integration with identity-centric and context-aware access policies, enabled by real-time telemetry, will further enhance security granularity and effectiveness. Enterprises should anticipate increased convergence between network functions and security enforcement, spurring innovation and delivering even more cost-effective, scalable, and robust solutions.
Conclusion
Secure Access Service Edge is more than a passing trend—it represents a fundamental shift in how enterprises approach networking and security in a cloud-first, remote-driven world. SASE enables organizations to simplify operations, reduce costs, and strengthen defenses against evolving threats by unifying connectivity and protection within a single, scalable framework. While adoption comes with challenges, careful planning, phased implementation, and strong collaboration between networking and security teams ensure a smoother transition. Future innovations in AI, automation, and identity-driven security will only expand SASE’s value, making it a cornerstone of digital resilience. Investing in SASE today positions businesses seeking to future-proof their operations to thrive in tomorrow’s complex digital landscape.